Thanks to Jyotirmoy Banik for sharing the URL about how could the Text of your Clipboard could be stolen while you might be visiting several websites and you forgot that you have already copied your Credit Card number or PIN number or Email address or Password for further use.
Copy any thing and go to URL: http://www.sourcecodesworld.com/special/clipboard.asp
You will see that they have retrieved your Clipboard information. It is easy to do while you are sufring using Internet Explorer (IE) , but not in Firefox or Opera.
It is true, text you last copied for pasting (copy & paste) can be stolen when you visit web sites using a combination of JavaScript and ASP (or PHP, or CGI) to write your possible sensitive data to a database on another server. Hopefully you haven't copied a credit card number recently before surfing!
Text From Your Clipboard - Source Code
The Clipboard hack is done by the following Source Code:
<Script Language="JavaScript">
var content = clipboardData.getData("Text");
alert(content);
</Script>
To avoid Clipboard Hack Problem of Internet Explorer (IE) , do the following:
1. Go to internet options->security
2. Press custom level
3. In the security settings, select disable under Allow paste operations via script.
Now the contents of your clipboard are safe. :)
Source: sourcecodesworld.com
Friday, October 27, 2006
Your Secured Information could be Hacked away
Tuesday, October 24, 2006
Software WAR!
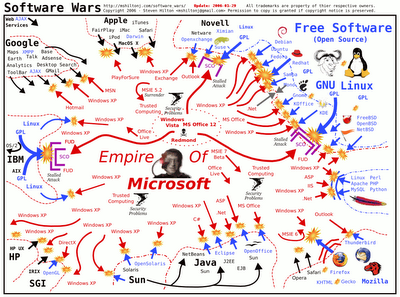 Last 2/3 days ago i found one of my friend sent me this funny image. But though most of the people calims it funny i feel that it's a real scenario of Software War in our current time.
Last 2/3 days ago i found one of my friend sent me this funny image. But though most of the people calims it funny i feel that it's a real scenario of Software War in our current time.
Microsoft is fighting with everyone in software industries and everyone is fighting with them with strong base. Think what if every one merges to kill down Microsoft? Then? What will be the ultimate result?
Click on the Picture to view in large size. You must enjoy it.
Sunday, October 22, 2006
Interview with Christopher Janz of PageFlakes
Interview with Christopher Janz of PageFlakes
By Kat Ortland

PageFlakes delivers a customized homepage that can be edited to include hundreds of unique widgets, RSS feeds, etc. & tabs for different content.
- What inspired you to create Pageflakes? Where did the idea come from?The idea of a personalized startpage itself is not new. Yahoo, Excite and others started personalizing their portals years ago. However, thanks to the rise of RSS, XML, APIs and AJAX and other new developments the value proposition is now much more compelling. It's these new developments as well as inspirations from other sites which made us come up with the idea for creating Pageflakes.
- How long did it take you, from start to finish, to get Pageflakes off the ground?About three months from scratch to Public Beta.
- How did you get funding for the project?So far we're self-funded but we plan to do a business angel or VC round shortly.
- How do you sustain the usage costs of Pageflakes?We expect advertising to be our most important revenue stream in the future. Subscription fees for premium fees are an option, but far in the future. Further revenue streams like licensing revenues are possible, but we don't have concrete plans on that yet. In general, generating revenue is not a short term priority for us. We really want to focus on developing the product and acquiring a large user base first.
- What programming languages & technologies does Pageflakes use?The Pageflakes framework is built using ASP.NET 2.0, Atlas, JavaScript and of course lots of AJAX goodness. The flakes are built using a variety of different languages and technologies. We wanted to make the framework as flexible as possible to allow each developer to use his favorite tools and technologies. So if you want to develop a flake, you can also use PHP, JSP or ASP.NET, and work with an IDE like VisualStudio.NET, or even develop flakes in Flash.
- How big is your development team? Anything special you'd like to say about them?Our core development team consists of three outstanding developers in Bangladesh. I myself do most of the UI/design/speccing stuff. In addition, we have a couple of freelancers across the globe.
They are geniuses. :-)
- What are your plans for the future of Pageflakes?Short term:
1. Continue to build an excellent product and innovate more quickly than the rest
2. Add new useful flakes every week
3. Release some really exciting features like the option to share and publish pagesLong term:
1. Provide users a convenient one-stop access point to all the services, apps and data they care about.
2. Simplify almost any aspect of peoples' digital lives. - How many people do you estimate currently use Pageflakes?We don't have much statistcis yet, since we launched the beta just a week ago. But yesterday an article in which we were mentioned got slashdotted, so we had about 20,000 visits yesterday.
- What is your opinion about the Web 2.0 phenomenon? How do you see Pageflakes fitting into it?I think there are a couple of viewpoints and angles that are new to Web 2.0 and that make it different. But frankly, I don't have a completely consistent picture of it yet or of what it will look like with hindsight. I'm also not sure how long the term "Web 2.0" will survive. It will probably be a temporary term because at some point people will start calling their startups "Web 3.0"... and then it will get weird.
There are a couple of interesting developments, technological and other, which fuel the development of new services. One of them, of course, is AJAX because, as you know, it allows a desktop-like user interface and user experience on the Web. AJAX is not that new, really, but frankly I'd never heard of it until a year ago or so.
The AJAX technology really fuels many of these applications because many of them aren't a lot of fun if you have to reload the page all the time. If you compare Gmail with the Web applications of a few years ago, I think the difference is huge.
Another very important trend is data syndication using RSS and XML and other formats, as well as the opening of applications using APIs, which fuel all those mashups and open forms and integrations with one another. This is pretty much the focus of our efforts since we provide users with a variety of applications and services and content offerings. While we created a variety of application of our own, many of them integrate with existing applications like Zoho Writer, Flickr, Del.icio.us, & Alexa.
So these two things are absolutely vital for us, (AJAX and Data Syndication) without them we wouldn't exist, so to speak. These are the things that make us different from old-school portals which also offered personalization but which have much less appeal.
- Do you have advice or insights for other people who are trying to create their own Web 2.0 projects?If you have a great idea, go for it! And choose your partners based on skills rather than geography even if people are telling you this can't work. Our founder team consists of five people from three continents who somehow found each other....and so far it works great
source: www.seomoz.org
Friday, October 13, 2006
OpenSource replacement - 001
 Today I saw a post in BDLUG ( Bangladesh Linux User Group ) where a person asked about if there is any opensource project, which could be the replacement of Microsoft Visio and Microsoft Projects?
Today I saw a post in BDLUG ( Bangladesh Linux User Group ) where a person asked about if there is any opensource project, which could be the replacement of Microsoft Visio and Microsoft Projects?
Mr. Jamil Ahmed replied him with the references of
- Planner : http://live. gnome.org/ Planner
So, I came up with thinking to share few list of OpenSource replacement of Costly Licensed Software. That's why i named this post as "OpenSource replacement - 001". Hope it could be a good start ;)
(To be continued)
Friday, October 06, 2006
Hackers Crash the Social Networking Party - [PC World]
Hackers Crash the Social Networking Party
Huge crowds in social networking sites draw money-minded malware authors.
malware authors.
Josh Krist, PC World
The malware headache began for Robyn when she saw a MySpace bulletin from a friend inviting her to view new photos. She knew the friend in real life, so she went ahead and clicked the link. The site looked like a photo-sharing site, but one she had never heard of. Then her computer practically froze. A few days later, her MySpace friends received photo-viewing invites that seemed to come from her.
"It definitely wigged me out," says Robyn, who asked that her last name not be used. She hasn't touched that computer since.
Like pickpockets at a festival, money-minded malware authors are drawn by the huge crowds visiting social networking sites. In an August report, Internet security firm ScanSafe states that, on average, one in every 600 pages on the sites hosts some form of malware. The report says Facebook tended to be more secure given its previous member restriction to those with educational e-mail addresses, but the site has since opened its doors to everyone.
And these days, those viruses and worms are after your wallet. "There's a great deal of money in it for people to be able to get your personal data," said Lysa Myers, virus research engineer for McAfee Avert Labs, in an e-mail interview.
Poisoned Banner Ads
One major attack took place in July, when iDefense, a research and security company, discovered a poisoned banner ad that appeared on MySpace, Webshots, and many other sites. The new type of attack ad downloaded adware onto an estimated million computers, according to iDefense. The threat went after low-hanging fruit by exploiting an image file (.wmf) vulnerability. It's a vulnerability that was reported and fixed way back in January. But in the huge numbers game of social networking sites, the attack still found plenty of victims.
And the game is growing ever larger. MySpace ranks as the sixth most-visited site in the world, according to Alexa.com, which analyzes Web traffic and puts Flickr at number 39 and Facebook at number 69. Most social networking sites more than doubled their user base between July 2005 and July 2006, according to comScore Media Matrix.
It's not just eager teens visiting the sites, either. The ScanSafe report found that social networking sites now account for 1 percent of at-work Web browsing. This may not seem like much, but consider just how much Web traffic goes in and out of most every business in the nation.
Good Defense Necessary
Even if the site maintainers are on the ball--MySpace generally gets decent marks for closing new-found holes and threats on its site--the sheer number of people involved can present an irresistible target for crooks. To keep your system safe, make sure you've got a layered defense with good antivirus and antispyware programs, and a firewall. PC World's Spyware and Security Info Center contains the latest security software reviews and rankings, and a link to our Internet Safety Tool Kit.
In addition, Dan Moniz, a security consultant in San Francisco, recommends using a browser other than Internet Explorer. "The way that Internet Explorer is hooked in with the operating system can cause some problems," he says. The July banner ad attack targeted Internet Explorer.
As if downloaded malware weren't enough, future attacks could twist things so that the browser attacks a site. At the BlackHat Internet security conference in Las Vegas this year, Moniz and HD Moore, head of the Metasploit project and a well-known hacker, presented a novel proof-of-concept hack. It showed that a poisoned site could infect a Web browser using Javascript such that the browser becomes an attacker and infects visited blogs or social networking sites. It could spam links to malware downloads or overwhelm blogs with casino advertisement comments, for instance.
Like many proof-of-concepts, this one might never become a real threat. It still has to find an open security hole to infect the browser in the first place, and it might never interest malware writers who have plenty of other profitable methods currently in use. But it's one more example of a party crasher just waiting to spoil the fun.
_________________________
source: PC World










![Validate my Atom 1.0 feed [Valid Atom 1.0]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiYD3hpgZLCZrqmc9-3M7Wxtu22I5T1dnXV8w0cL-nAXezEFvrlTAyFxz2ut8fewe2nQbwPyHlr6dQVceLkp7GPjzowzhTDTjOcfWizKPNwJDFp0MN-AeylCLNnwm_JBKLlhOHB/s400/valid-atom.png)

